使用整个多云环境的可见性杜绝企业暴露风险
了解 企业的云资源
通过上下文可见性了解访问和暴露风险路径,发现云中的计算、身份和数据资产。
发现 关键云风险
获取上下文信息,对云错误配置、过度访问权限、漏洞和暴露的敏感数据中的风险进行优先级分析。
化解 云风险暴露问题
通过快速、精确地化解最重要的暴露风险,即使时间有限,也可快速降低云风险。
获取完整的云生命周期可见性
统一代码、云和运行时的可见性,揭示来自密钥、错误配置、漏洞和身份问题的风险并对这些风险进行优先级分析。使用 Tenable Cloud Security 的内置云基础设施和授权管理 (CIEM),AppSec 和 SecOps 团队可以实施最小特权原则,并从基础设施即代码 (IaC) 到生产环境中更快地实施修复。

全面的清单
动态攻击面映射
预测优先级分析
动员和修复
高级分析和报告
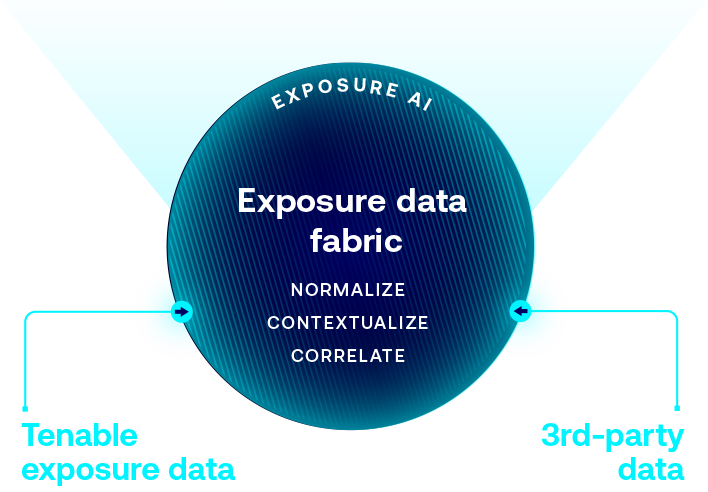

借助生成式 AI 加快搜索、洞察与行动速度,揭示隐藏的风险,并提升您整个环境中的安全专业能力。
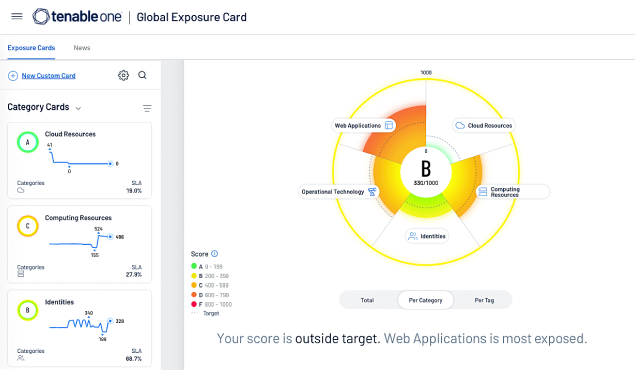
获取整个攻击面上所有资产和风险的统一视图:不可见的资产、IT、OT、IoT、云、身份和应用程序。
通过对跨域关系可视化来了解攻击者的可访问性,从而阻断最为重要的攻击路径。
专注处理最重要的事情:攻击者最可能利用的重要风险暴露。
使用自动化工作流和规范性指导,加快响应速度,从而简化修复工作。
使用与业务保持一致的视图简化网络风险暴露的度量和沟通,对决策和投资加以优化。
利用全球最大的资产、风险暴露和威胁上下文的信息库,赋予 ExposureAI 无与伦比的洞察力。
组织数据以减少冗余,并提高完整性、一致性和效率。
使用额外的洞察信息丰富数据,使其更具可操作性和实用性。
识别并向核心业务服务与职能部门呈现重要的关系上下文信息。
将安全嵌入软件开发生命周期 (SDLC) 的每个阶段,确保代码、IaC、容器和 API 全都得以安全开发和维护
化解 DevOps 和 SecOps 之间的孤岛效应,获得对开发生命周期本身的运营可见性和事件响应功能。
识别和修复所有动态、临时云资产中的错误配置、身份滥用和工作负载漏洞
常见问题
什么是 Tenable Cloud Security?
-
将强大的云安全态势管理 (CSPM) 和云安全工作负载保护 (CWP) 功能相结合的 Tenable Cloud Security 是一款完全集成的云基础设施安全解决方案,其中包含同类最佳的云基础设施授权管理 (CIEM)、云检测和响应 (CDR) 技术以及高度创新的基础设施即代码 (IaC) 安全和 Kubernetes 安全态势管理 (KSPM) 解决方案。云原生应用保护平台 (CNAPP) 可管理您的多云清单,在整个堆栈中强制实施预防性安全策略(解决身份、网络、数据和计算风险),检测和应对实时威胁,将安全左侧并通过 IaC、CI/CD 或运行时环境自动修复风险。这样可根据安全标准进行基准评估,促进在企业中强制实施合规性。
Tenable Cloud Security 如何定价和授予许可?
-
Tenable Cloud Security 包括所有 CNAPP 组件,也可以作为单独的产品或作为 Tenable One 的一部分购买。单独定价根据计费资源的数量进行。然后根据预测的每月总用量提供批量折扣。同样,如果包含在 Tenable One 中进行定价,基本定价基于可计费资源总数。然后,使用云资源在 Tenable One 中的比率对云资源进行定价,之后使用现有 Tenable One 许可下订购的总资产提供批量折扣。可以对即时 (JIT) 访问单独授予许可,也可以添加到单独产品中或作为 Tenable One 一部分进行定价的产品中。如需定制的定价信息或有疑问,请联系 Tenable 代表。
我能在何处找到 Tenable Cloud Security 的文档和版本说明?
-
Tenable 产品的技术文档位于 https://docs.tenable.com。您必须登录 Tenable Cloud Security 帐户才能查看版本说明和文档。如需访问技术文档和版本说明,请联系 Tenable 代表。
Tenable Cloud Security 和 Tenable One 有何不同?
-
Tenable Cloud Security 可以作为单独的产品或作为 Tenable One 暴露风险安全管理平台的一部分进行购买。在与 Tenable One 结合使用时,Tenable Cloud Security 可为整个 IT 环境提供全面的视图,包括传统网络、本地服务器、运营技术和公有云。通过作为 Tenable Cloud Security 的一部分购买 Tenable One,企业可将其 Tenable 购买的产品整合到一份合同中,并访问其他功能,如风险暴露视图。
Tenable Cloud Security 与哪些云和云原生工具相集成?
-
Tenable Cloud Security 与所有主要的云提供商(AWS、Azure、GCP)集成,此外还集成了许多云提供商服务,如 AWS Control Tower 和 Entra ID。将 Tenable Cloud Security 与工单、通知和 SIEM 工具相集成,可支持创建工单和发送推送通知,并利用标准通信工具(如 Jira、Slack、Microsoft Teams 和电子邮件集成工具)在企业内扩展工具。
Tenable Cloud Security 支持哪些身份提供商?
-
Tenable Cloud Security 与许多 IdP 集成,包括 Entra ID、Google Workspace、Okta、OneLogin 和 Ping Identity。这些 IdP 集成可显示与云帐户相关联的联合用户和组的完整清单,并提供权限分析和身份情报。
Tenable Cloud Security 如何保护我的数据?
-
Tenable 可确保工作负载的安全,并采用强大的加密和访问控制来保护敏感数据。它会对过度权限和长期访问权限的授予加以限制。Tenable 可缩小数据外泄时的爆炸半径,从而保护您的敏感数据。有关 Tenable Cloud Security 如何确保您独有云环境的数据保护和隐私的更多信息,请联系您的 Tenable 代表。
我能否在不涉及第三方的情况下使用 Tenable Cloud Security?
-
可以。 Tenable Cloud Security 用户可以购买帐户内扫描功能作为其环境的附加组件。该功能支持对遵守严格数据隐私标准和法规的企业的工作负载进行现场扫描。 帐户内扫描功能在云帐户中执行,数据永远不会离开环境。
我如何购买 Tenable Cloud Security?
-
要购买 Tenable Cloud Security,您可以与当地的认证合作伙伴接洽,或联系您的 Tenable 代表。单击此处申请演示 Tenable Cloud Security。
相关资源
了解更多关于 Tenable Cloud Security 的信息
用 [Tenable 的] 自动化技术可以让我们免去繁琐的人工流程,在几分钟内即可完成原本需要两三个安全人员花费好几个月才能完成的工作。
- Tenable Cloud Security