使用 Tenable 简化 Azure 云安全
从构建到运行时,全面掌握 Azure 云可见性
借助 Tenable Cloud Security,可保护企业整个开发生命周期,提升团队的 Microsoft Azure 安全专业能力,并促进云团队、开发团队以及身份和访问管理 (IAM) 团队之间的协作效率。

“只需点击两次,我们就能了解 Azure 云中的实际情况,
这对我们来说极具价值。”
工业服务提供商的业务解决方案主管
减少 Azure 与多云环境中的风险暴露
深入理解 Azure 架构,弥合安全缺口
Tenable Cloud Security 采用自动化、“身份优先”的整体方法,通过精准的风险检测、指导性修复以及大规模最小特权管控,为企业团队赋能。 通过发现漏洞,并结合整个多云与混合环境的上下文对漏洞进行优先级分析,评估 Azure 资源的风险。
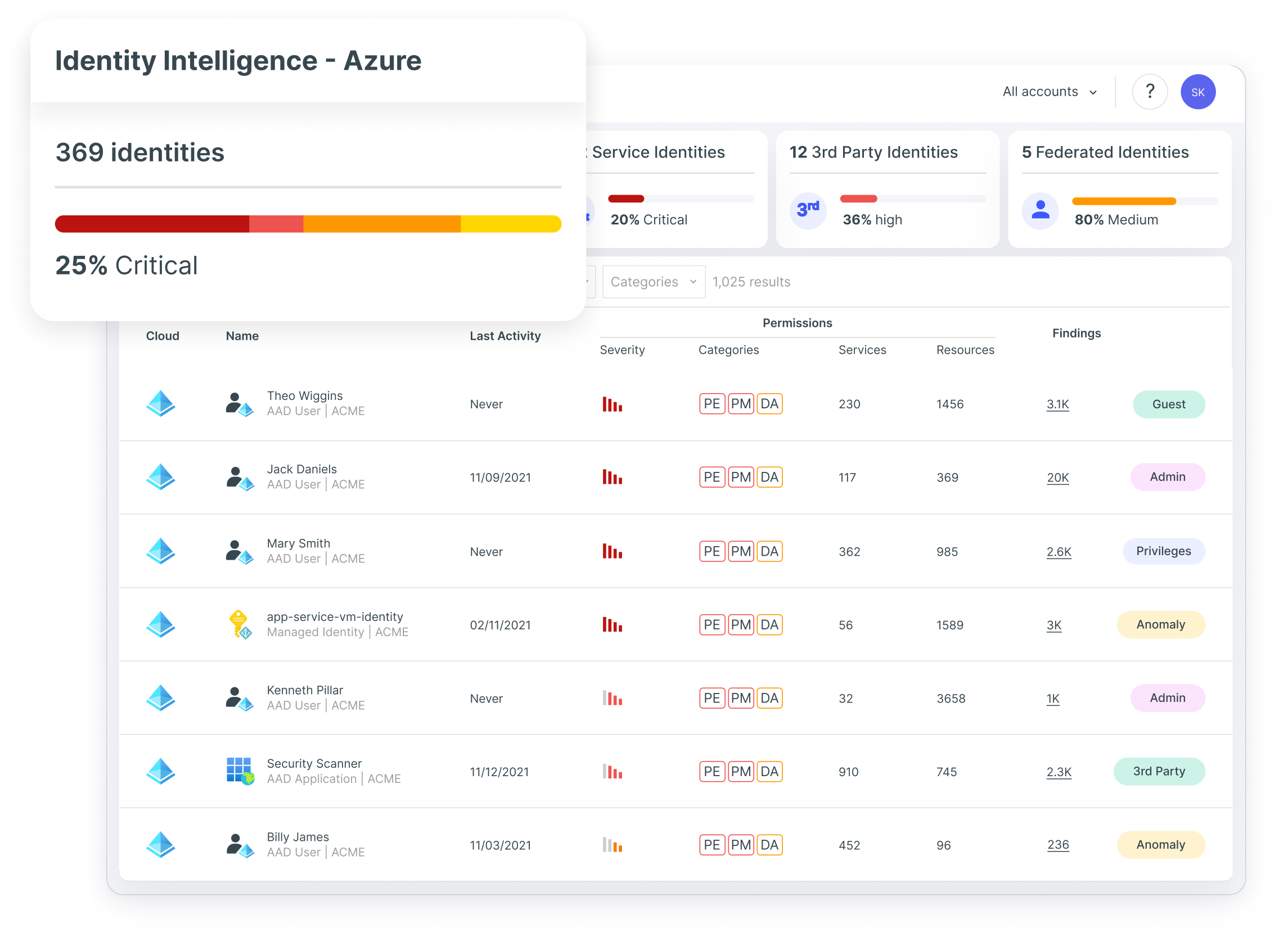
借助 Azure 集成强化云应用程序安全
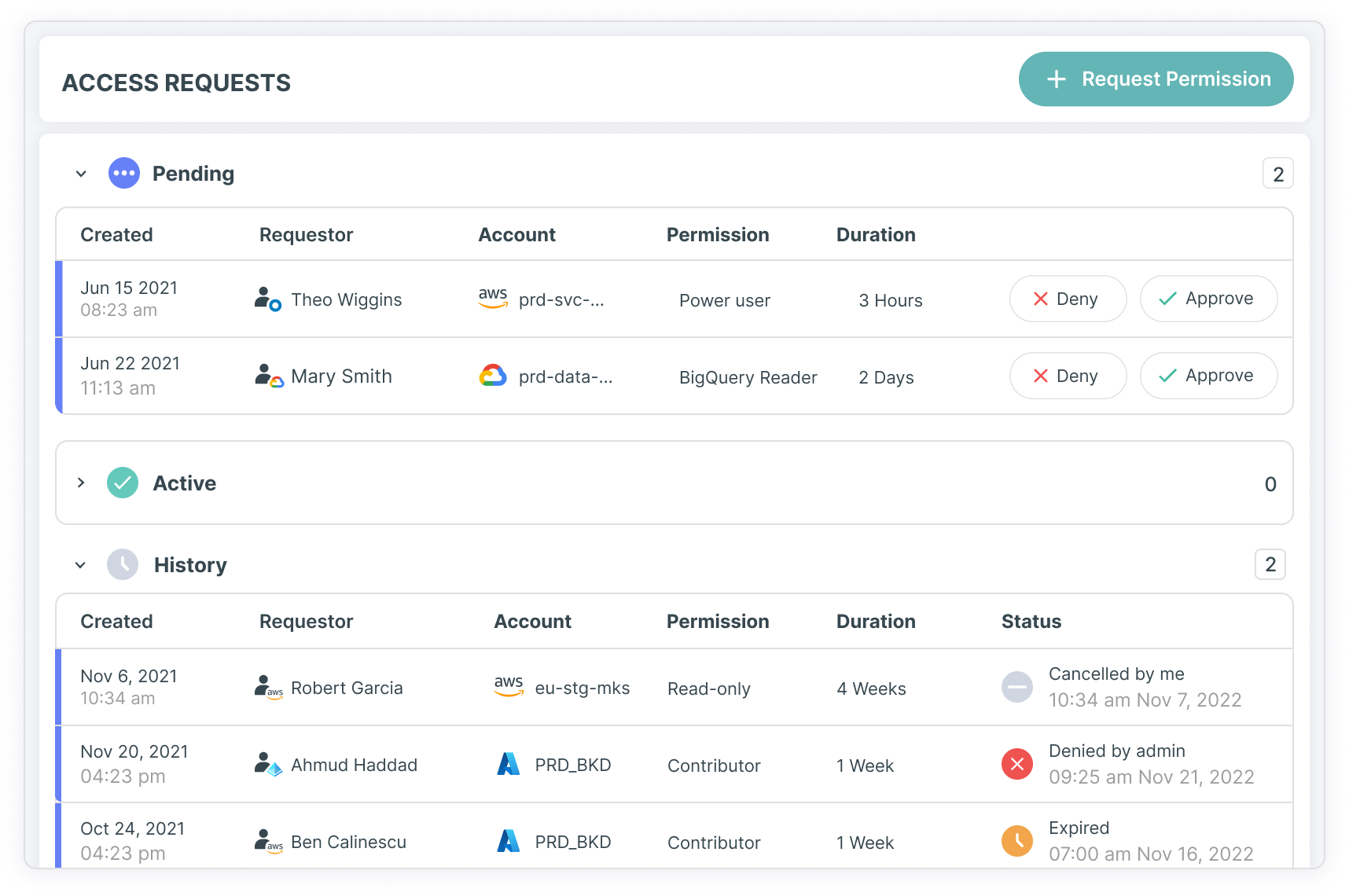
Tenable 助力安全团队强化 Azure 环境中的云应用安全,有效应对关键的基础设施即服务 (IaaS) 风险(如身份、访问权限和特权错误配置等)。 通过与 Entra ID、Azure Pipelines 等原生功能集成,以保护身份和访问管理 (IAM) 生命周期,企业可借助精准可视化、准确优先级分析及指导性修复,缩小 Azure 与多云环境中的攻击面。
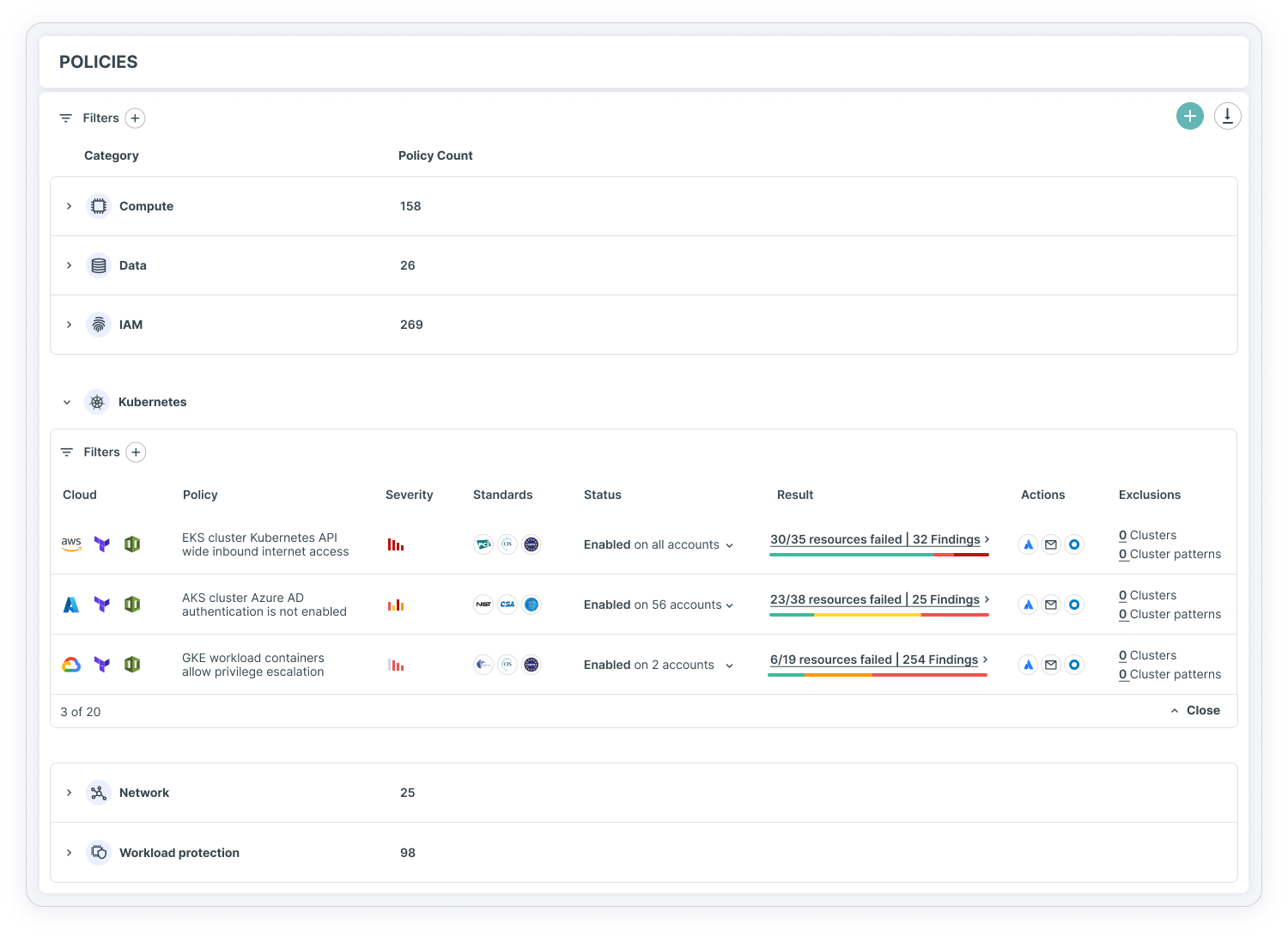
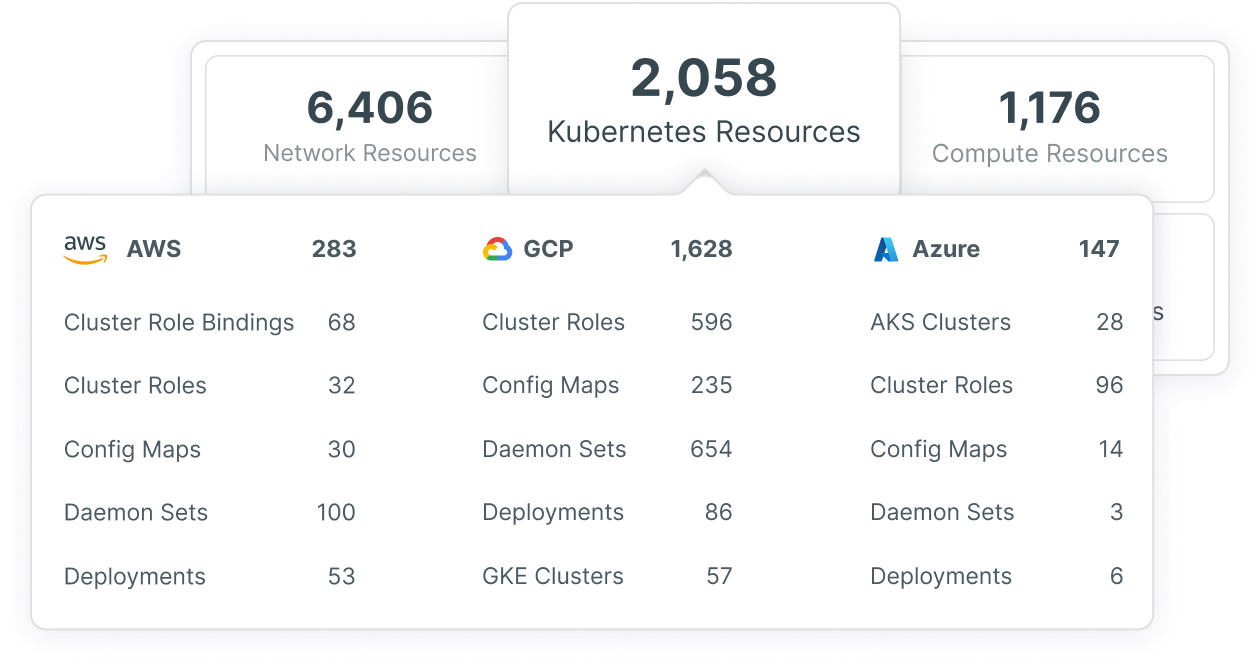
全方位强化各环境中的 AKS 集群安全
查看 Azure Kubernetes 集群的状态、配置及风险情况。 通过动态风险评估,明确哪些集群需要立即修复,以及哪个团队负责执行修复操作。
了解更多关于 Tenable Cloud Security 的信息
用 [Tenable 的] 自动化技术可以让我们免去繁琐的人工流程,在几分钟内即可完成原本需要两三个安全人员花费好几个月才能完成的工作。
- Tenable Cloud Security