Tenable Cloud Vulnerability Management:降低云时代的漏洞风险

Tenable 已推出 Tenable Cloud Vulnerability Management 解决方案,这是 Tenable One 平台内的一款功能强大的全新产品,旨在帮助漏洞管理负责人识别和修复多云及混合环境中的暴露风险问题,并对其进行优先级分析。
要点
- 无代理清单与可见性: 无需部署代理或转移帐户外数据,即可在 AWS、Azure、Oracle Cloud 和 GCP 等平台上,实现所有现有虚拟机、虚拟机映像和容器映像的完整资产清单与覆盖。
- 统一的混合风险视图:将虚拟机和映像安全数据整合到 Tenable One 平台中,生成单一、统一的资产暴露风险评分 (AES),为整个攻击面提供即时、关联上下文的风险洞察。
- 指导式修复与暴露风险管理路径:获取化解风险所需的清晰修复步骤,为未来构建全面的暴露风险管理计划奠定基础。
漏洞管理团队多年来一直在完善其管理计划。凭借一流的流程、专业知识和技术,团队擅长定位并修复那些会给本地资产带来风险的最关键漏洞。但显然,云环境是另一番截然不同的场景。
企业的云原生开发速度持续加快。云工作负载和容器在几分钟内就能完成创建与销毁。企业清楚需要扩展现有管理计划,以避免云漏洞成为危险的安全盲点。
要是能将现有的一流漏洞管理计划直接扩展到云环境中,该多好?要是能为云工作负载和容器获得所需的基础安全保障,又该多好?
我们倾听了企业的需求,并且很高兴地宣布,现在企业可以轻松实现上述目标了。
正因如此,我们无比激动地宣布推出 Tenable Cloud Vulnerability Management 解决方案,这是我们 Tenable One 暴露风险安全管理平台中的一款全新产品。

Tenable One 的实力在实践中彰显:Tenable Cloud Vulnerability Management 通过优先级分析和统一报告来明确暴露风险情况,可即时统一本地、云环境和混合环境中的漏洞风险可见性。
Tenable Cloud Vulnerability Management 旨在帮助企业识别和修复云漏洞,并对其进行优先级分析,同时支持基础的云工作负载保护 (CWPP) 实践。
日益扩大的云漏洞缺口
随着企业加速采用云和 AI 技术,安全防护的发展速度却未能跟上。 来自《2025 年 Tenable 云 AI 风险报告》的以下数据表明,即便是 AI 关联工作负载中的一个暴露风险点,也可能引发连锁反应,导致重大风险:
- 70% 的云 AI 工作负载包含至少一个未修复的关键漏洞,这一比例远高于非 AI 工作负载中 50% 的同类问题占比。
- 在使用 Amazon SageMaker 的企业中,91% 至少有一台笔记本实例启用了有风险的根访问权限默认设置。
- 14% 的 Amazon Bedrock 用户至少一个 AI 训练存储桶缺少公共访问阻止机制。
由于 AI 驱动的应用程序催生了新的依赖关系,并扩大了攻击面,企业在本地与云环境中能够看到的风险,与攻击者能够利用的风险之间,在可见性和优先级分析方面的缺口正不断扩大。要填补这一缺口,关键在于将漏洞管理与云安全统一在单一、关联上下文的暴露风险视图之下,使 CISO 和安全团队都能清晰、快速地采取行动。
Tenable Cloud Vulnerability Management 简介
Tenable Cloud Vulnerability Management 填补了这一缺口。它为 AWS、Azure、Oracle Cloud Infrastructure (OCI) 和 Google Cloud 提供无代理的多云覆盖能力,通过 Tenable One 平台内的原生 API 连接,提供近实时的可见性和风险评估。
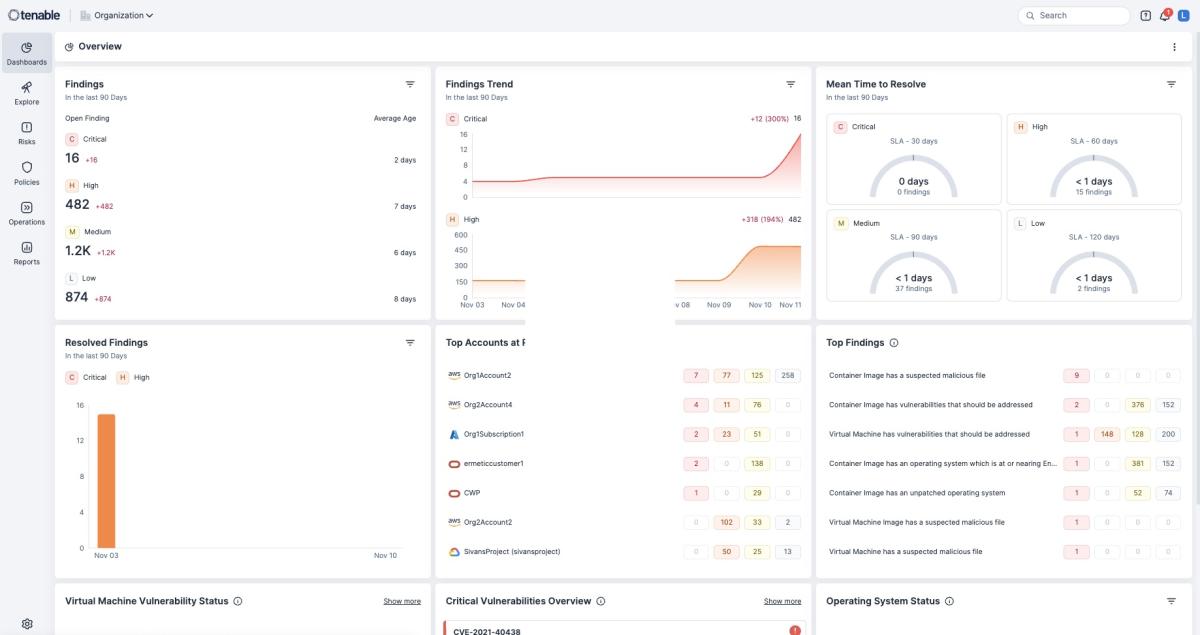
全新的 Tenable Cloud Vulnerability Management 许可证可在 Tenable Cloud Security 仪表盘中,直接提供所有基于云的虚拟机、机器映像 (AMI) 和容器映像的无代理清单,并附带清晰、指导式的风险修复步骤。
借助 Tenable Cloud Vulnerability Management,漏洞管理负责人能够:
- 轻松实现混合环境的无代理清单覆盖。评估整个多云和混合环境中的工作负载与容器,无需应对运维难题。通过利用云原生 API,Tenable 在帐户内进行数据分析,确保持续、准确的覆盖,且无需部署代理,也无需将敏感数据转移到帐户外进行扫描。
- 保护注册表中的容器。Tenable Cloud Vulnerability Management 在容器生命周期的关键阶段,即注册表扫描阶段,提供全面的漏洞扫描功能。扫描存储在注册表(无论是 AWS Elastic Container Registry (ECR) 等托管服务还是第三方容器注册表)中的容器映像。这能让企业在映像被拉入实时运行时环境之前,识别并解决漏洞问题。
- 获得现代安全所需的全面、统一风险视图。Tenable Cloud Vulnerability Management 与 Tenable One 暴露风险安全管理平台无缝集成。这种集成可将新的云安全发现结果,与来自 Tenable One 各组件(如用于本地的 Tenable Vulnerability Management、Identity Exposure、OT Security 和 Web Application Scanning)的数据即时结合。该平台的统一性不仅实现了真正的混合环境可见性,还能过滤掉无关干扰信息。
这意味着,企业可将现有的漏洞管理实践扩展到云环境中,而无需面对传统基于代理的解决方案所带来的复杂性、延迟或安全盲点。
为何无代理可见性能改变一切
与传统漏洞扫描程序不同,Tenable Cloud Vulnerability Management 无需在数千个工作负载中部署或维护代理。它利用云原生 API 连接到各个帐户、捕获快照,并在需要时解密卷,从而快速、全面地洞察软件包、文件签名和漏洞情况。
在不影响生产工作负载性能的前提下,Tenable Cloud Vulnerability Management 为漏洞管理负责人提供以下能力:
- 跨帐户和跨区域的即时启用
- 严格确保隐私合规的帐户内数据分析
- 漏洞的全面管理和优先级分析
结合 Tenable 的漏洞优先级评级 (VPR)(这是一个由全球最全面的漏洞情报数据库之一提供支持的预测模型),企业能够根据可利用性、成熟度和威胁上下文,精准定位哪些暴露风险最为关键。
可见性与上下文结合:从当前需求出发,随业务成长扩展
借助 Tenable Cloud Vulnerability Management,如今便可着手解决关键的云漏洞问题。例如,该平台能即时发现存在关键漏洞(这类漏洞有已知的利用方法且 VPR 评分较高,如运行着未修复零日漏洞的旧操作系统)的实时虚拟机。随后,企业可以在攻击者利用该缺陷之前找到并修复这一有重大影响的问题,从而立即获得保护。
同时,Tenable Cloud Vulnerability Management 是暴露风险安全管理平台 Tenable One(该平台提供了可扩展的发展路径)的一部分。它统一了 IT、云、身份和运营技术 (OT) 领域的可见性,并支持叠加更多功能(包括用于身份风险的 CIEM、用于敏感数据的 DSPM 等),无需从零开始,即可构建全面的 Continuous Threat Exposure Management (CTEM) 计划。 漏洞数据不再只是一份缺陷清单,它会结合错误配置、暴露风险情况和运营风险进行分析。
换言之,借助 Tenable Cloud Vulnerability Management,企业可以从现在开始保护云工作负载,并为未来构建全面的 CTEM 计划找到清晰的路径。
了解详情
- Cloud
- Risk-based Vulnerability Management



