Tenable versus CrowdStrike Falcon Exposure Management
Proactively secure your attack surface — not just your endpoints
Tenable has defined proactive security with best-in-class vulnerability management for more than two decades. And now, we are leading the way to exposure management. While CrowdStrike specializes in reactive incident response with endpoint detection and response (EDR), we enable security leaders to identify, prioritize and mitigate cyber risks effectively before attackers can exploit them.
请参阅 Tenable 实际应用案例
是否希望了解 Tenable 如何帮助团队揭示和解决将企业置于危险境地的重大网络漏洞?
填写此表格,获取定制报价或演示。
Why customers choose Tenable over CrowdStrike
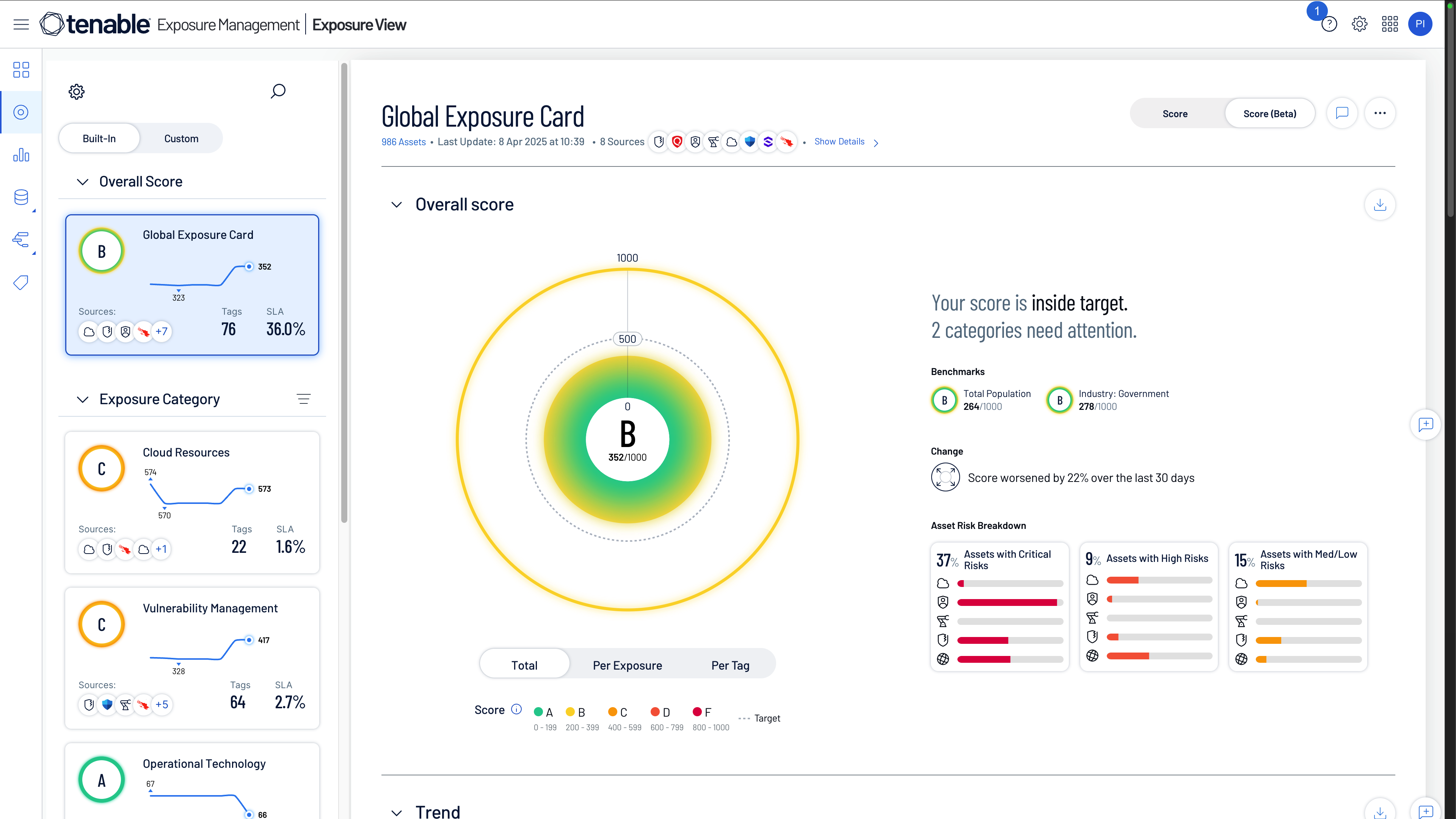
Compare Tenable Exposure Management
to CrowdStrike Falcon Exposure Management
Core focus
Unified exposure across IT, cloud, identity, and OT
Exposure from endpoint and identity telemetry
风险暴露管理分析
Combines integrated metrics across risk-based vulnerability management, web app scanning (WAS), cloud security, identity exposure, OT security, EASM and third-party data
Lacks comprehensive network scanning, web app security (WAS), identity data and holistic context beyond endpoints
资产清单
Unified asset graph across IT, cloud, OT, and identities
Based on discovered external and managed endpoint assets
Exposure Response
Exposure Response to track risk remediation with SLAs — instead of cumulative risk scores — and a single end-to-end workflow and a risk-based approach, regardless of patch availability
未提供
合规
Covers a wide variety of compliance frameworks across various OSs
Limited support for CIS benchmarks
同行业者基准测试
Comparison of cyber risk to industry peers and to quickly identify shortcomings and strengths
未提供
Coverage scope
Coverage for a wide variety of asset types — endpoints, network devices, OT, cloud workloads, web apps
Primarily focused on endpoints with a Falcon agent and network devices visible to a Falcon agent
Scanning technology
Agent-based, agentless and network scanning
Agent-based and network scanning for devices visible to a Falcon agent
Tool consolidation potential
High—replaces scanners, CSPM, IAM risk tools, attack graphing, custom dashboards
Low—adds exposure context to Falcon but doesn’t replace core security tools
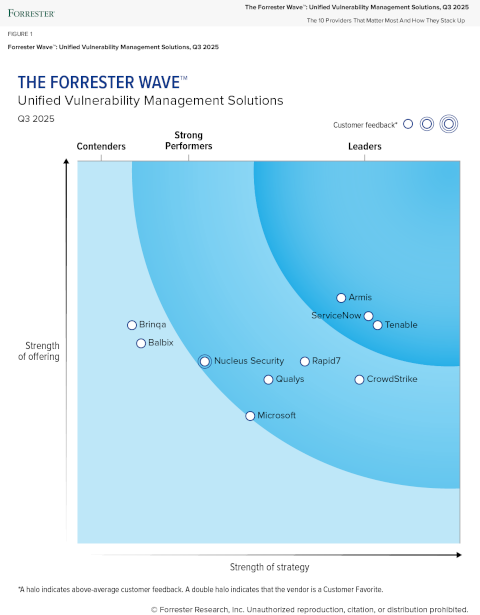
See why Tenable is a leader in vulnerability management
2025 年第 3 季度“Forrester Wave ™: Unified Vulnerability Management”报告
Tenable continues to extend its established vulnerability assessment offerings into exposure management with its Tenable One platform
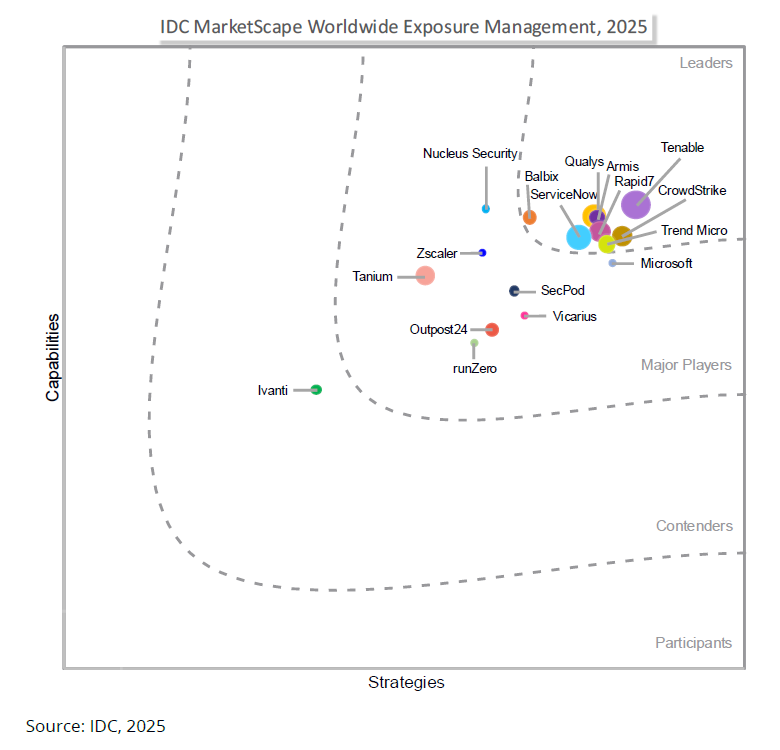
Tenable 荣获 IDC 报告“IDC MarketScape Worldwide Exposure Management 2025 Vendor Assessment”评选的领导者称号。
“企业在寻求可以涵盖 IT、云、OT/IoT、身份和应用程序环境的统一暴露风险管理平台时,应对 Tenable One 予以考虑。”(Tenable 译文)
阅读报告开始使用 Tenable One
Tenable One 已帮助我们的工程师将手动任务所花的时间降低 75%,这样工程师便可集中精力进行实际的工程设计工作。