使用 Tenable Cloud Security 管理身份治理
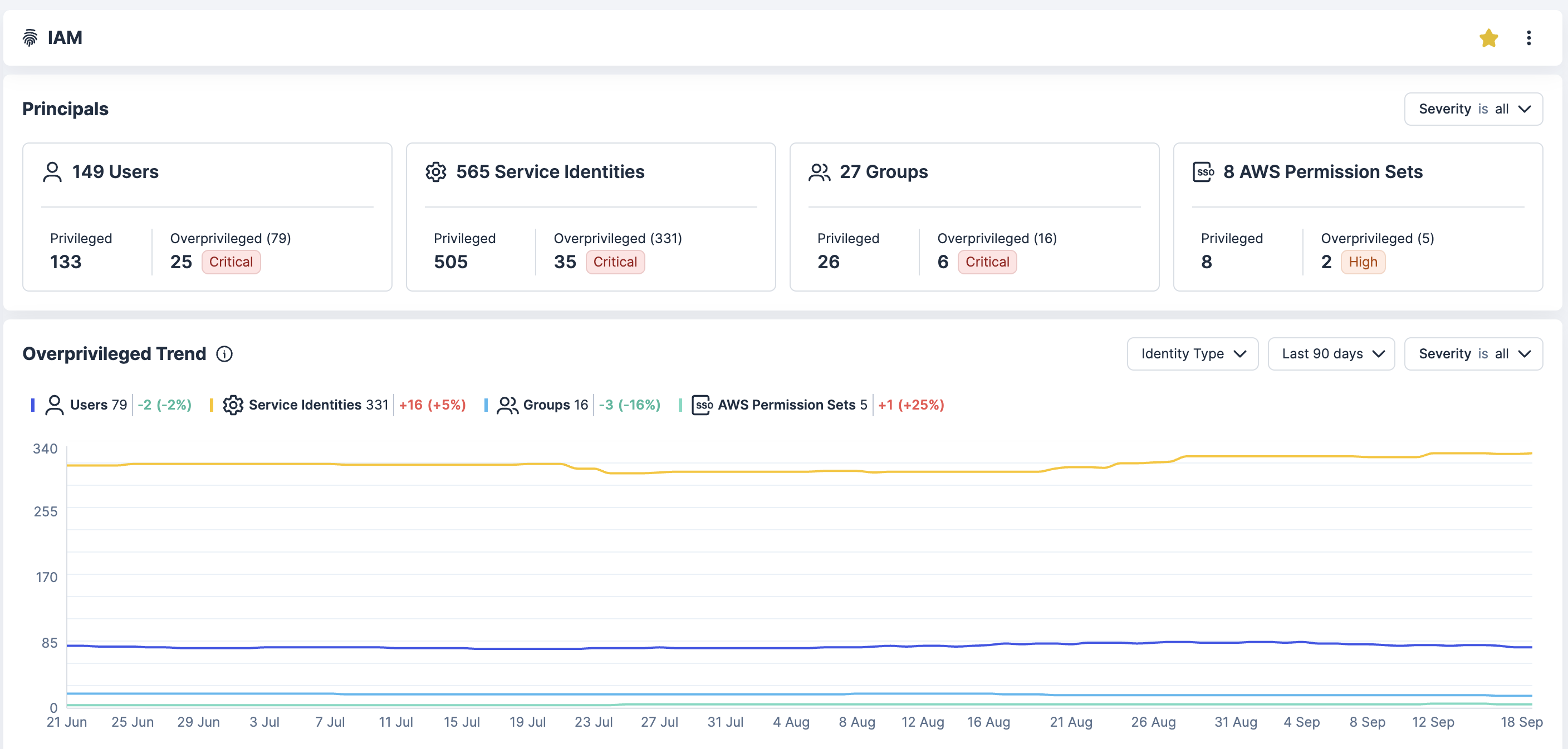
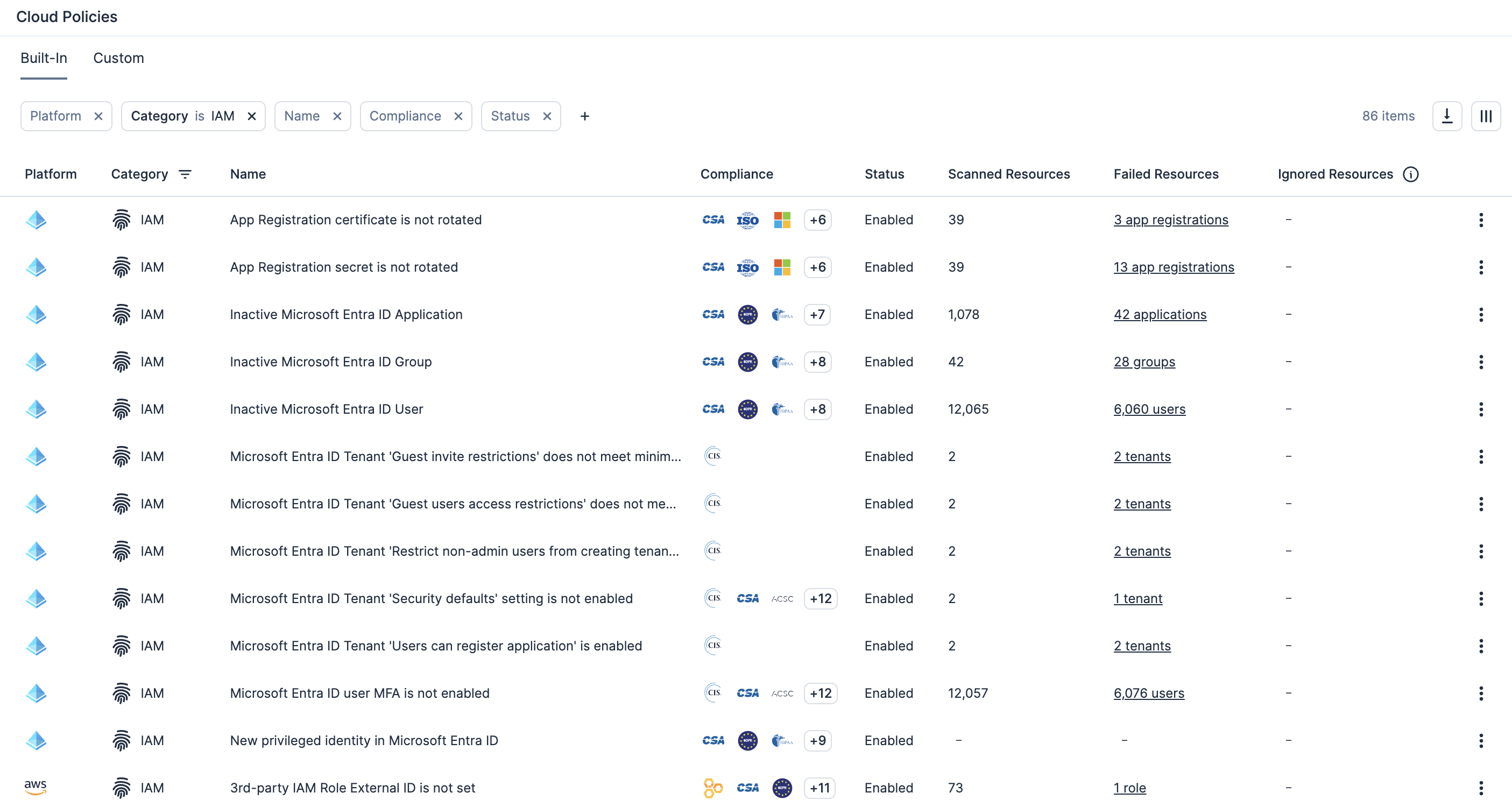
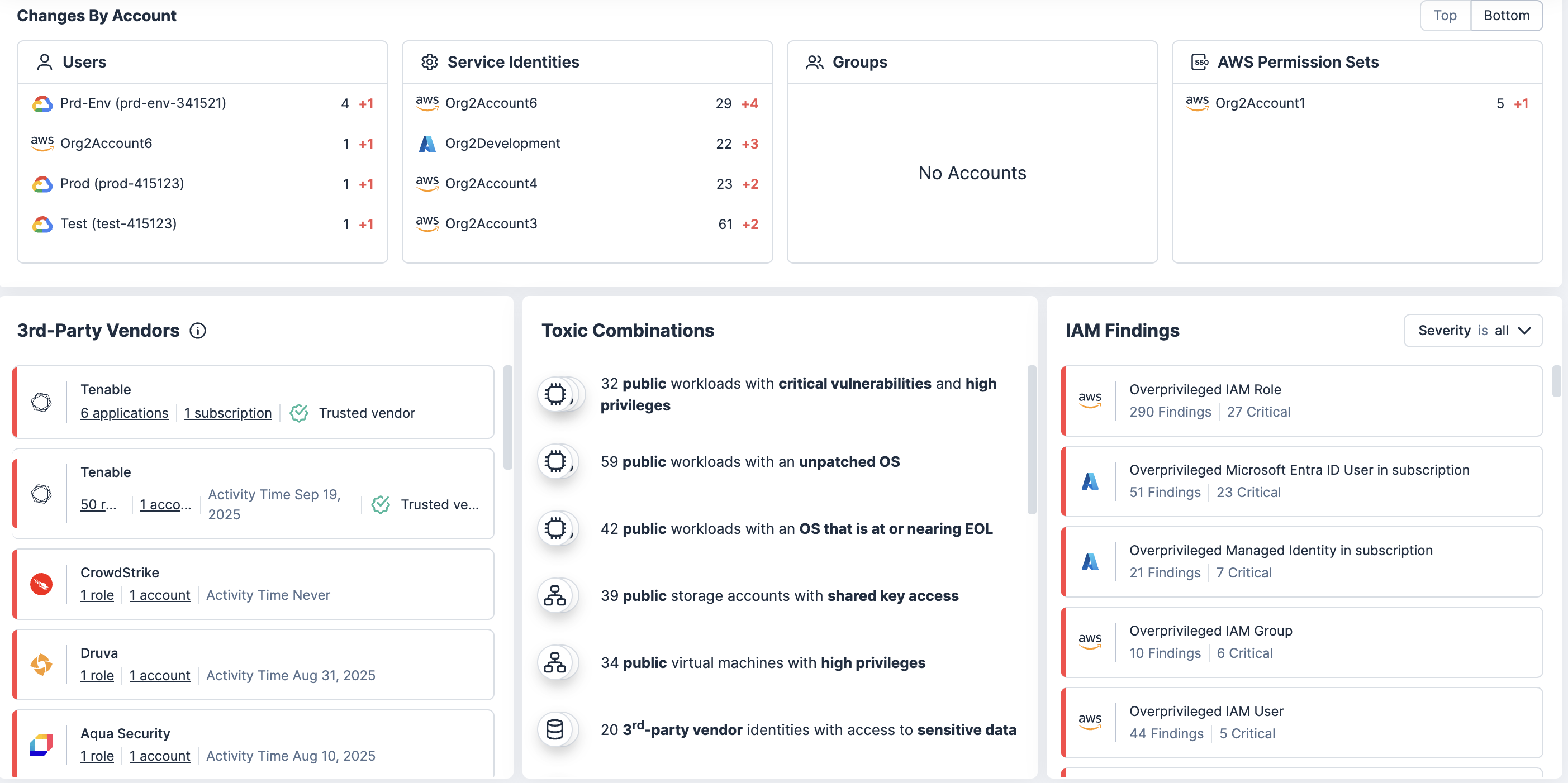
减少过度的云权限,这是造成数据外泄和审计失败的主要原因。缩小身份爆炸半径,通过可见性、自动化和策略实施来符合最小特权最佳实践。
将 CIEM 与 Tenable One 集成
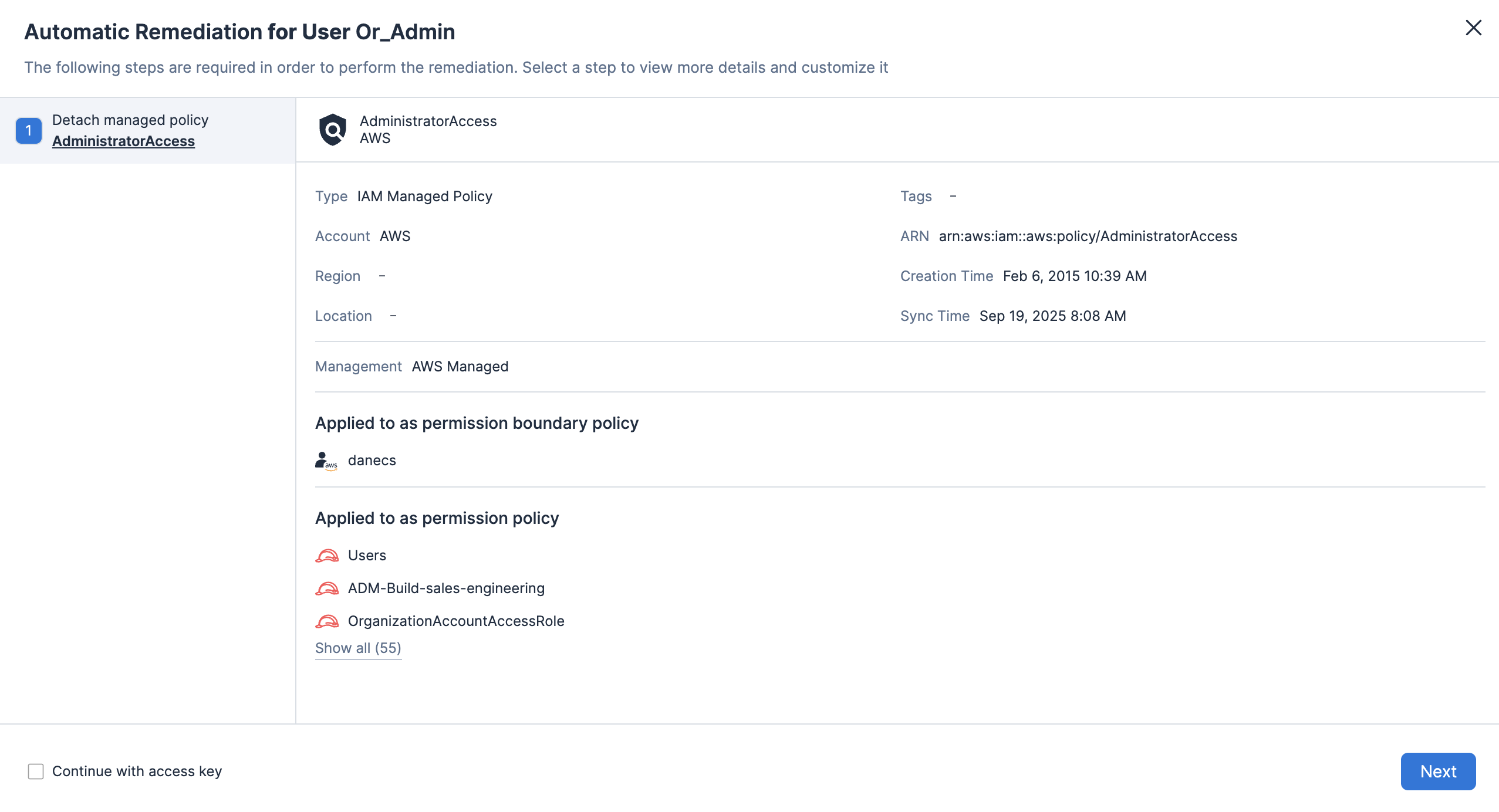
使用云基础设施授权管理 (CIEM) 持续实施最低特权,确保权限分配恰到好处、即时且从不过度。
了解更多关于 Tenable Cloud Security 的信息
用 [Tenable 的] 自动化技术可以让我们免去繁琐的人工流程,在几分钟内即可完成原本需要两三个安全人员花费好几个月才能完成的工作。
- Tenable Cloud Security