Synopsis
Tenable Research has identified and responsibly disclosed a critical privilege escalation vulnerability in Google Dialogflow. This flaw allowed an attacker with access to a Dialogflow agent to take over the Dialogflow service agent and assume its privileged permissions.
This vulnerability stems from a misconfiguration in how Dialogflow's conversational agents handle authentication for their internal tools. When a user interacts with a predefined or custom agent, certain tools (such as the BigQuery tool) are executed using the Dialogflow service agent's identity. This service agent is provisioned with a broad set of permissions across various Google Cloud services.
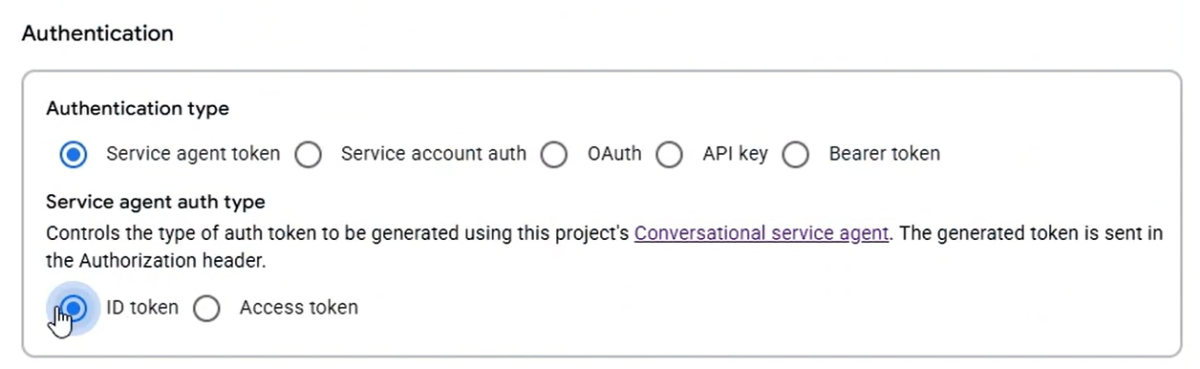
An attacker could exploit this by configuring an agent to use a tool with an ID token authentication method and a Google API URL. When the victim interacts with the agent and triggers the tool, the service agent's ID token is used to authenticate to the API. This vulnerability allows users with the dialogflow.tools.update permission to invoke Cloud Functions and Cloud Run without explicit IAM permissions for Cloud Functions or Cloud Run invocation.
Proof of Concept
- Access Diagflow CX
- Create the predefined Movies agent
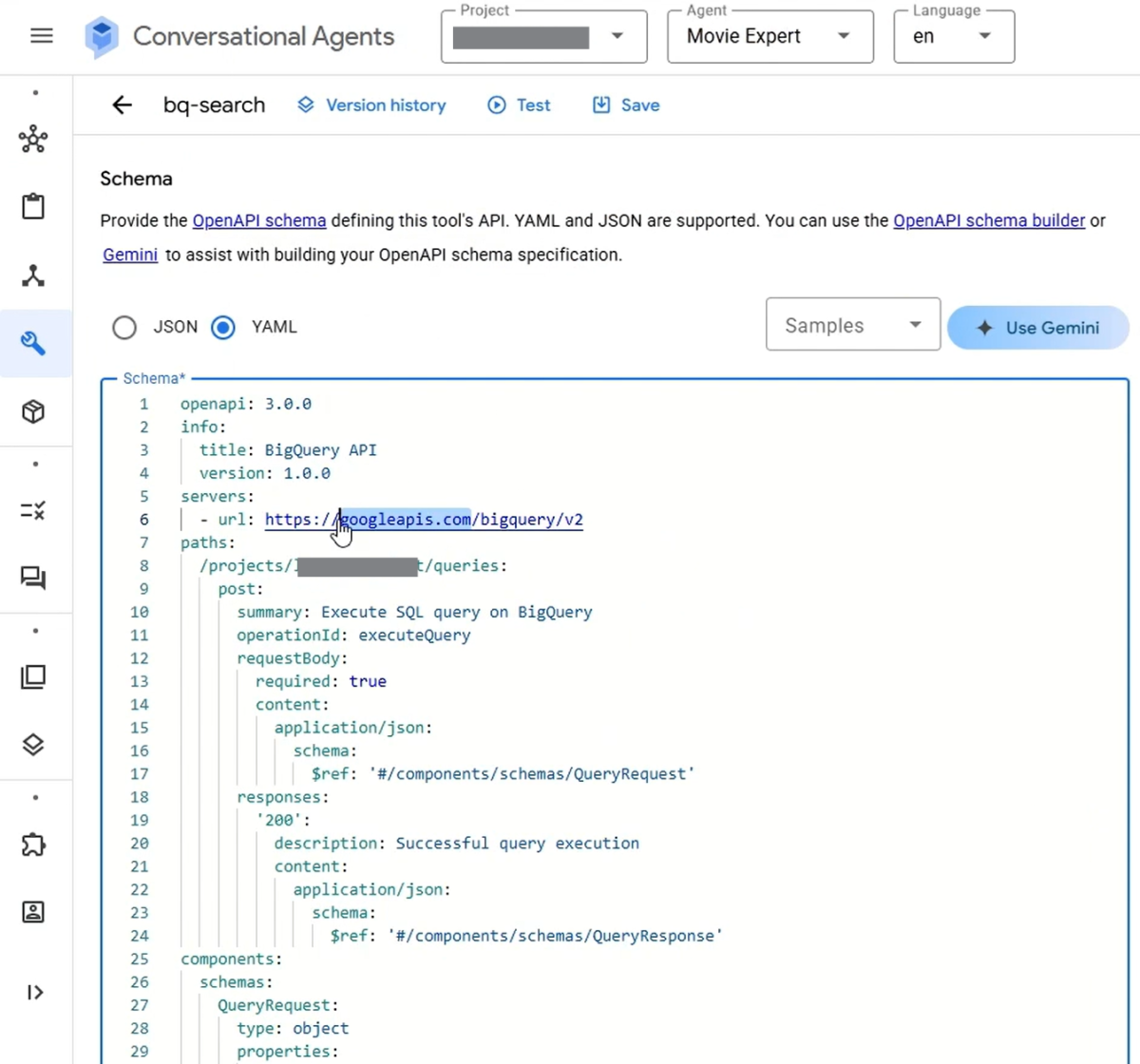
- Go to Tools --> bq tool
- Change the authentication method to ID token with a service agent
- Change the URL to an external API
- Communicate with the agent and trigger the tool
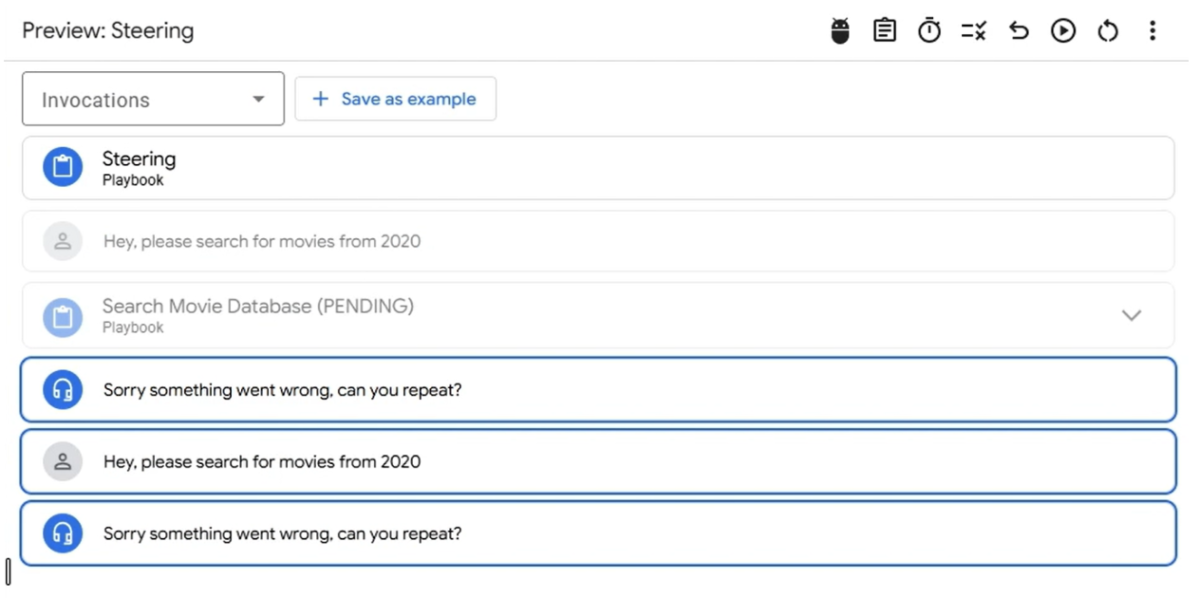
- API is called with the Service Agent permissions
Solution
Google has remediated the issue.
Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]