F5 BIG-IP Breach: 44 CVEs That Need Your Attention Now

Partnering with an EDR vendor after a nation-state has already stolen your source code isn’t innovation — it’s a gamble. You don’t build a fire extinguisher while the house is burning. You find every spark before it becomes the next inferno.
Key takeaways:
- F5’s BIG-IP is used to secure everything from government agencies to critical infrastructure.
- The theft of BIG-IP source code and undisclosed vulnerabilities by a nation-state actor is a five-alarm fire for national security and puts all organizations at risk.
- We provide detailed steps Tenable customers can take immediately, as well as general guidance on how organizations can protect themselves now and in the long term.
The breach of F5’s BIG-IP product development environment is a five-alarm fire for national security and once again raises doubts about the safety of the software supply chain.
Among the data stolen in the nation-state attack: source code for BIG-IP networking solutions as well as undisclosed security vulnerabilities that were under investigation. According to F5’s October 15 8-K filing with the U.S. Securities and Exchange Commission (SEC), some of the exfiltrated files from its knowledge management platform contained configuration or implementation information for a small percentage of customers. The company also rotated its signing certificates and keys on October 13.
F5’s BIG-IP isn't just another piece of software. It is a foundational element in the technology stack used to secure everything from government agencies to critical infrastructure. In the hands of a hostile actor, this stolen data is a master key that could be used to launch devastating attacks, similar to the campaigns waged by Salt Typhoon and Volt Typhoon. We haven’t seen a software supply chain compromise of this scale since SolarWinds.
The implications are far-reaching. BIG-IP is used by approximately 57,000 companies; while the majority are in the $1 million – $10 million revenue range, F5 says its products are used by 85% of the Fortune 500. Affected products include BIG-IP (F5OS), BIG-IP (TMOS), Virtual Edition (VE), BIG-IP Next, BIG-IQ, and BIG-IP Next for Kubernetes (BNK) / Cloud-Native Network Functions (CNF).
For a full list of CVEs associated with this incident, see Frequently Asked Questions About The August 2025 F5 Security Incident.
While F5 has not observed evidence of modified source code or a supply-chain attack, the stolen data could potentially be used to develop new exploits for unpatched vulnerabilities. In response, F5 released security patches on October 15.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive requiring that all organizations with F5 products apply these updates immediately. “The alarming ease with which these vulnerabilities can be exploited by malicious actors demands immediate and decisive action from all federal agencies,” said CISA Acting Director Madhu Gottumukkala in a follow-up statement. “These same risks extend to any organization using this technology, potentially leading to a catastrophic compromise of critical information systems. We emphatically urge all entities to implement the actions outlined in this Emergency Directive without delay.” The U.K.’s National Cyber Security Center (NCSC) also issued an alert about the incident.
This incident does not affect Tenable products but we have released new plugins and additional guidance to help organizations secure their environments.
Organizations using F5 BIG-IP are advised to update the software as soon as possible, harden any public-facing BIG-IP devices, and remove any unsupported devices from their networks. The company said it is “partnering with CrowdStrike to extend Falcon EDR sensors and Overwatch Threat Hunting to BIG-IP for additional visibility and to strengthen defenses. An early access version will be available to BIG-IP customers and F5 will provide all supported customers with a free Falcon EDR subscription.”
While we applaud F5’s transparency and efforts to help organizations respond to the incident, this is not the time for experimentation. You don’t build a fire extinguisher while your house is burning. Likewise, waiting for an endpoint detection and response (EDR) vendor to build a solution after a threat actor has already accessed your most sensitive environment is ill-advised. The nation-state actor has been embedded in F5’s environment for some time, with access to highly sensitive data. They can act on what they’ve accessed at any time. Moreover, threat actors have repeatedly demonstrated their ability to disable EDR tools, thereby evading endpoint-based detection methods and rendering them largely useless.
The following key actions required by CISA in its mitigation guidance extend well beyond the capabilities of EDR:
- Inventory: Identify all instances of F5 BIG-IP hardware devices and F5OS, BIG-IP TMOS, Virtual Edition, BIG-IP Next, BIG-IP IQ software, and BNK / CNF.
- Harden public-facing hardware and software appliances: Identify if physical or virtual BIG-IP devices exposed to the public internet provide public access to the networked management interface.
- Update instances of BIG-IP hardware and software applications: Apply the latest vendor updates by Oct. 22, 2025, for the following products: F5OS, BIG-IP TMOS, BIG-IQ, and BNK / CNF — validate the F5 published MD5 checksums for its software image files and other F5 downloaded software. For other devices, update with the latest software release by Oct. 31, 2025, and apply the latest F5-provided asset hardening guidance.
- Disconnect end-of-support devices: Disconnect all public-facing F5 devices that have reached their end-of-support date. Report mission-critical exceptions to CISA.
- Mitigate against cookie leakage: If CISA notifies an agency of a BIG-IP cookie leakage vulnerability, the agency shall follow CISA’s accompanying mitigation instructions.
- Report: Submit a complete inventory of F5 products and actions taken to CISA by 11:59 p.m. EDT, Oct. 29, 2025.
We cannot stress enough the importance of finding and fixing the 44 CVEs associated with this incident immediately. Doing so requires visibility into areas of your infrastructure that can’t be reached by the “good enough” vulnerability scanning tools available from endpoint vendors. The immediate need is for effective triage.
Below, we provide detailed guidance on steps Tenable customers can take immediately. (Non-Tenable customers can start a free trial of Tenable Vulnerability Management today to see where they’re impacted so they can swiftly take action.)
Longer term, organizations need to prepare for the likelihood of nation-state actors leveraging additional F5 vulnerabilities for initial access, after which they will pivot to Living off the Land techniques to stealthily execute commands, establish persistence, move laterally, and escalate privileges. We’ve seen examples of such activity with Salt Typhoon and Volt Typhoon. Once it occurs, it becomes very difficult to detect and eradicate the actor. More guidance on preventive measures can be found below in the section “How do I protect my organization from the long-term impact of the F5 BIG-IP breach?”
I’m a Tenable Vulnerability Management customer. What should I do today?
Here are two examples of how to use Tenable Vulnerability Management to quickly find F5 BIG-IP in your environment and identify the related CVEs. A full list of CVEs associated with this incident can be found here. The inventory plugin for remote BIG-IP Web Management Interface is available here.
The screenshot below shows how you can quickly filter for the F5 BIG-IP version using plugin id: 76940 . This allows you to quickly see the version and the installed modules of your F5 device.
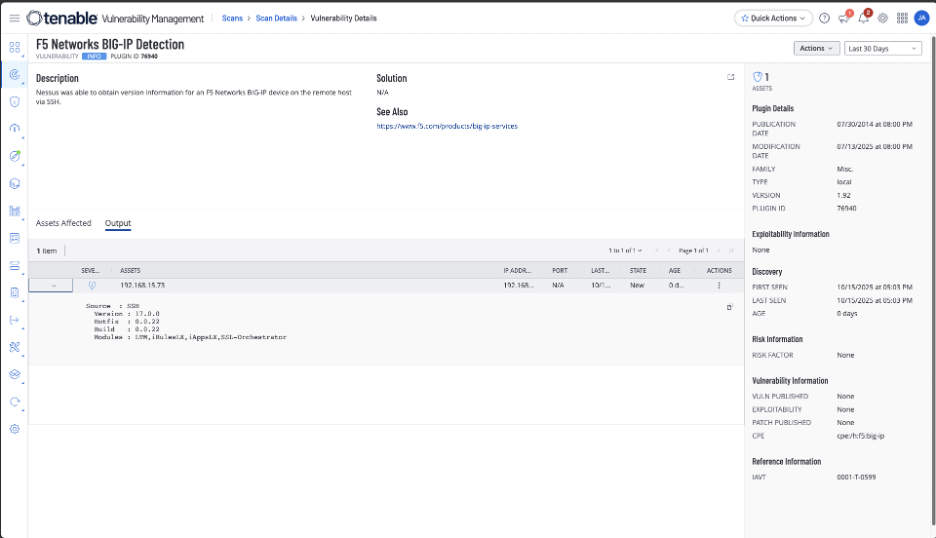
The screenshot below shows how you can see all known vulnerabilities for your F5 device. You can filter for CVEs and export the data to engage the various teams for remediation.
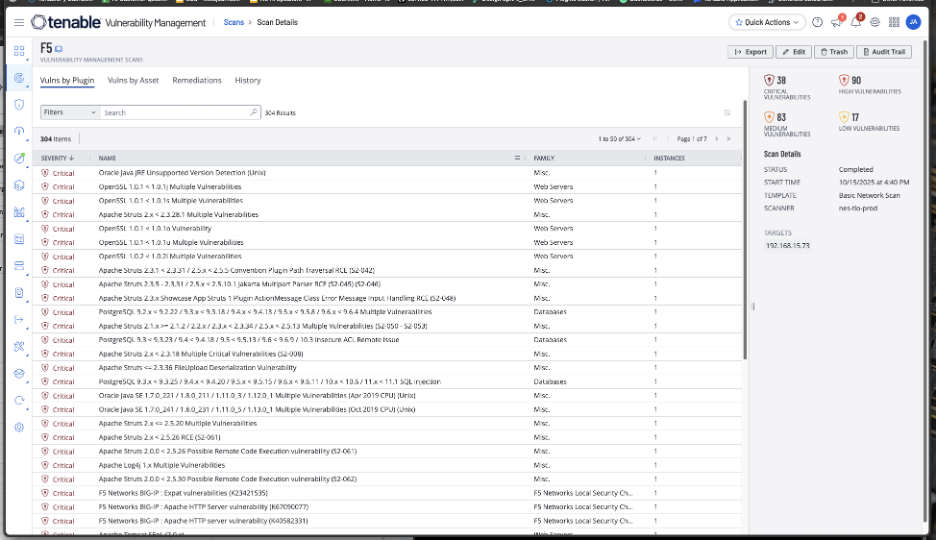
How do I protect my organization from the long-term impact of the F5 BIG-IP breach?
In addition to applying the urgent mitigations above, organizations need to be on alert for any infiltration attempts. Organizations are urged to take the following actions:
- Inventory all F5 assets in your environments. Tenable Vulnerability Management can provide a detailed and comprehensive inventory of your F5 assets as part of its network-wide scanning. It identifies F5 devices through methods like active scanning, passive monitoring, and credentialed scans, collecting detailed information about the asset, including its configuration and vulnerabilities. This granular level of discovery goes beyond simple asset lists to give you a clear, actionable view of every F5 device on your network.
- Continuously monitor assets in cloud, IT and OT environments. Tenable Vulnerability Management offers continuous monitoring across diverse environments, including IT, cloud, and OT. By deploying Tenable agents on transient devices, performing active scans on traditional IT assets, and using passive monitoring for sensitive OT systems, Tenable Vulnerability Management ensures you have an always-on, real-time assessment of your security posture, regardless of where the assets reside.
- Correlate data from asset inventories, vulnerability assessments, and security operations for a unified view of risk. Tenable Vulnerability Management is designed to be a central hub for vulnerability data. It correlates data from its own asset discovery and vulnerability assessments to provide a unified view of risk. It can also integrate with other security tools and CMDBs to enrich asset data and streamline remediation workflows.
- Incorporate threat intelligence feeds to understand which threats are most likely to be exploited and what risks they pose to your unique environment. Tenable utilizes a risk-based prioritization approach to help you focus on the most dangerous threats. It combines its Vulnerability Priority Rating (VPR) with your unique environmental context to provide a single, dynamic score that reflects the true risk of a vulnerability. This allows you to move beyond static, generic scores like CVSS and focus remediation efforts on the issues that are most likely to be exploited in the wild, enabling you to reduce your organization's overall cyber risk more effectively.
Learn more
- Join Tenable's Research Special Operations team to discuss the F5 incident in our Tenable Connect: Threat Roundtable.
- Start a free trial of Tenable Vulnerability Management today.
- Exposure Management
- Vulnerability Management


