Microsoft’s August 2025 Patch Tuesday Addresses 107 CVEs (CVE-2025-53779)

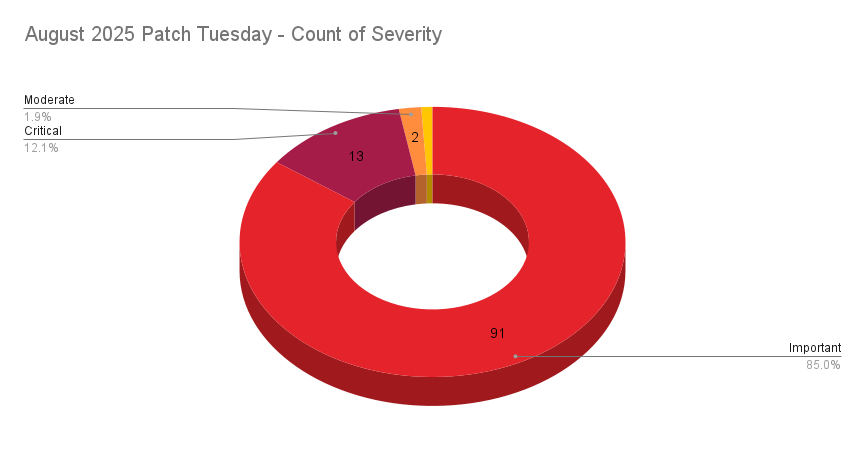
- 13Critical
- 91Important
- 2Moderate
- 1Low
Microsoft addresses 107 CVEs, including one zero-day vulnerability that was publicly disclosed.
Microsoft patched 107 CVEs in its August 2025 Patch Tuesday release, with 13 rated critical, 91 rated as important, one rated as moderate and one rated as low.
This month’s update includes patches for:
- Azure File Sync
- Azure OpenAI
- Azure Portal
- Azure Stack
- Azure Virtual Machines
- Desktop Windows Manager
- GitHub Copilot and Visual Studio
- Graphics Kernel
- Kernel Streaming WOW Thunk Service Driver
- Kernel Transaction Manager
- Microsoft 365 Copilot's Business Chat
- Microsoft Brokering File System
- Microsoft Dynamics 365 (on-premises)
- Microsoft Edge for Android
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Teams
- Remote Access Point-to-Point Protocol (PPP) EAP-TLS
- Remote Desktop Server
- Role: Windows Hyper-V
- SQL Server
- Storage Port Driver
- Web Deploy
- Windows Ancillary Function Driver for WinSock
- Windows Cloud Files Mini Filter Driver
- Windows Connected Devices Platform Service
- Windows DirectX
- Windows Distributed Transaction Coordinator
- Windows File Explorer
- Windows GDI+
- Windows Installer
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Media
- Windows Message Queuing
- Windows NT OS Kernel
- Windows NTFS
- Windows NTLM
- Windows PrintWorkflowUserSvc
- Windows Push Notifications
- Windows Remote Desktop Services
- Windows Routing and Remote Access Service (RRAS)
- Windows SMB
- Windows Security App
- Windows StateRepository API
- Windows Subsystem for Linux
- Windows Win32K GRFX
- Windows Win32K ICOMP
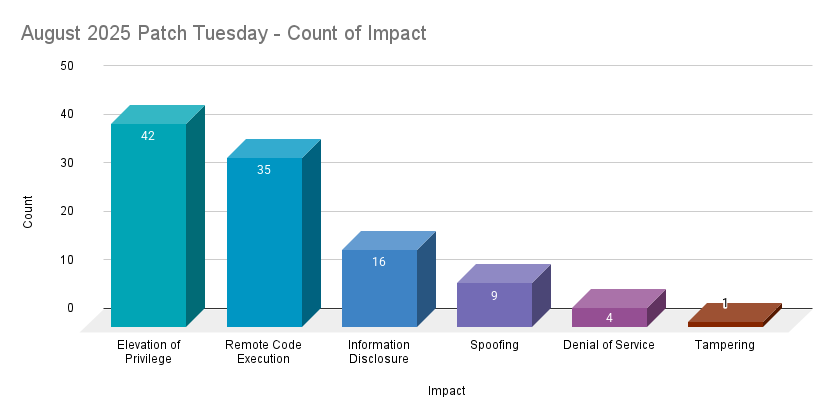
Elevation of privilege (EoP) vulnerabilities accounted for 39.3% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 32.7%.
CVE-2025-53779 | Windows Kerberos Elevation of Privilege Vulnerability
CVE-2025-53779 is an EoP vulnerability in Windows Kerberos. It was assigned a CVSSv3 score of 7.2 and is rated moderate. An authenticated attacker with access to a user account with specific permissions in active directory (AD) and at least one domain controller in the domain running Windows Server 2025 could exploit this vulnerability to achieve full domain, and then forest compromise in an AD environment.
This is a patch for a zero-day vulnerability dubbed BadSuccessor by Yuval Gordon, a security researcher at Akamai. It was disclosed on May 21. For more information on BadSuccessor, please review our FAQ blog, Frequently Asked Questions About BadSuccessor.
CVE-2025-49712 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2025-49712 is a RCE vulnerability in Microsoft SharePoint. It was assigned a CVSSv3 score of 8.8 and is rated important. An attacker would need to be authenticated with Site Owner privileges at minimum. Once authenticated, an attacker could either write arbitrary code or use code injection to execute code on a vulnerable SharePoint Server to gain RCE.
This RCE follows on the heels of the ToolShell vulnerabilities that were disclosed in the July 2025 Patch Tuesday release and exploited in the wild as zero-days.
CVE-2025-53778 | Windows NTLM Elevation of Privilege Vulnerability
CVE-2025-53778 is an EoP vulnerability affecting Windows New Technology LAN Manager (NTLM). It was assigned a CVSSv3 score of 8.8 and is rated as critical. According to the advisory, successful exploitation would allow an attacker to elevate their privileges to SYSTEM. This flaw was assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
This marks the second critical EoP affecting Windows NTLM in 2025, following CVE-2025-21311 which was patched in the January 2025 Patch Tuesday release.
CVE-2025-50177, CVE-2025-53143, CVE-2025-53144 and CVE-2025-53145 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
CVE-2025-50177, CVE-2025-53143, CVE-2025-53144 and CVE-2025-53145 are RCE vulnerabilities in Microsoft Message Queuing (MSMQ). While three of these four CVEs (CVE-2025-53143, CVE-2025-53144 and CVE-2025-53145) were assigned CVSSv3 scores of 8.8 and rated as important, CVE-2025-50177 was assigned a CVSSv3 score of 8.1 and rated as critical. Similarly, CVE-2025-50177 was assessed as “Exploitation More Likely,” while the other three were assessed as “Exploitation Less Likely.”
In order to exploit these CVEs, an attacker would need to send a crafted MSMQ packet to a vulnerable server in order to achieve code execution.
Tenable Solutions
A list of all the plugins released for Microsoft’s August 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's August 2025 Security Updates
- Tenable plugins for Microsoft August 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management

