识别和修复云错误配置
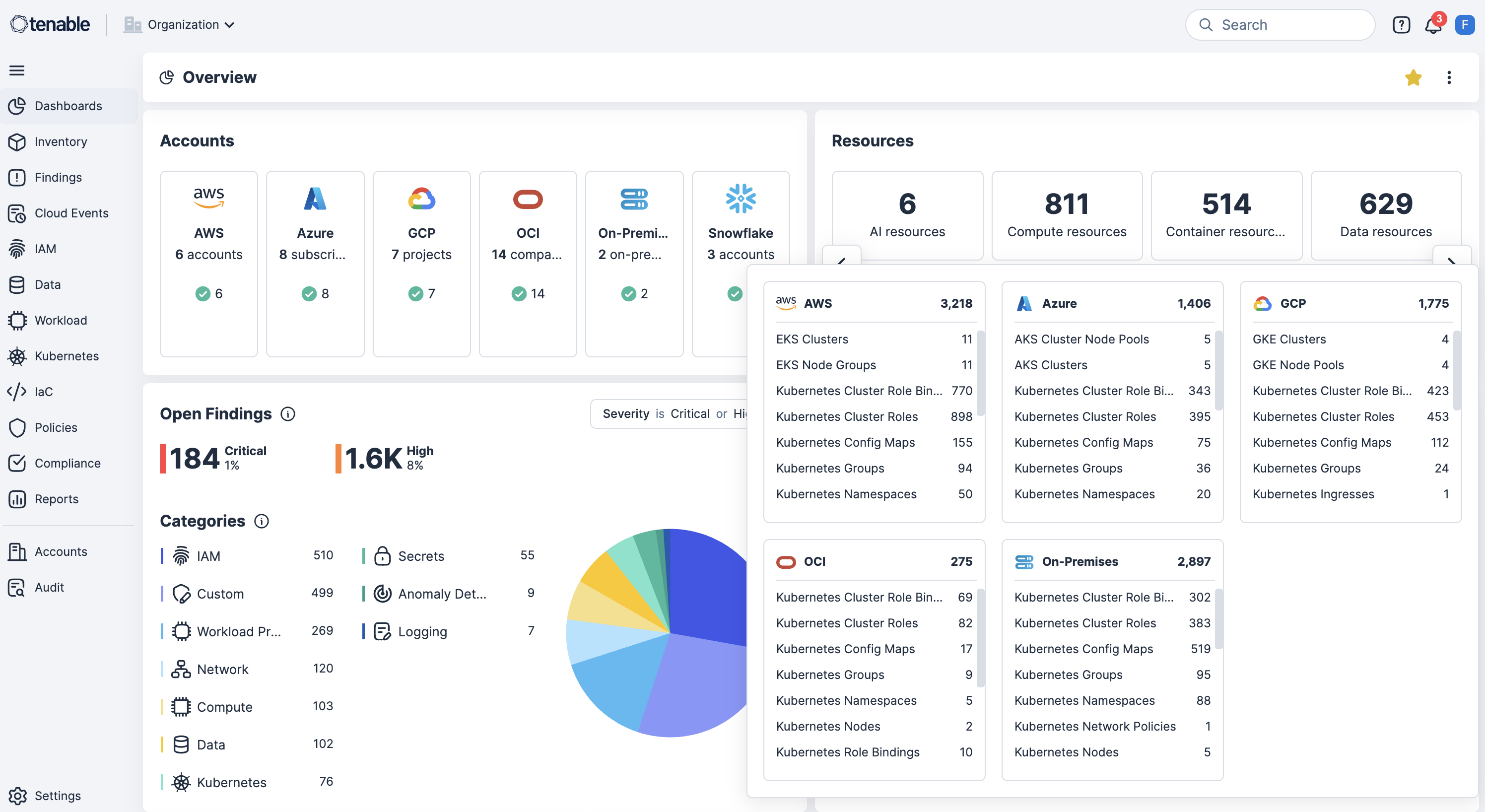
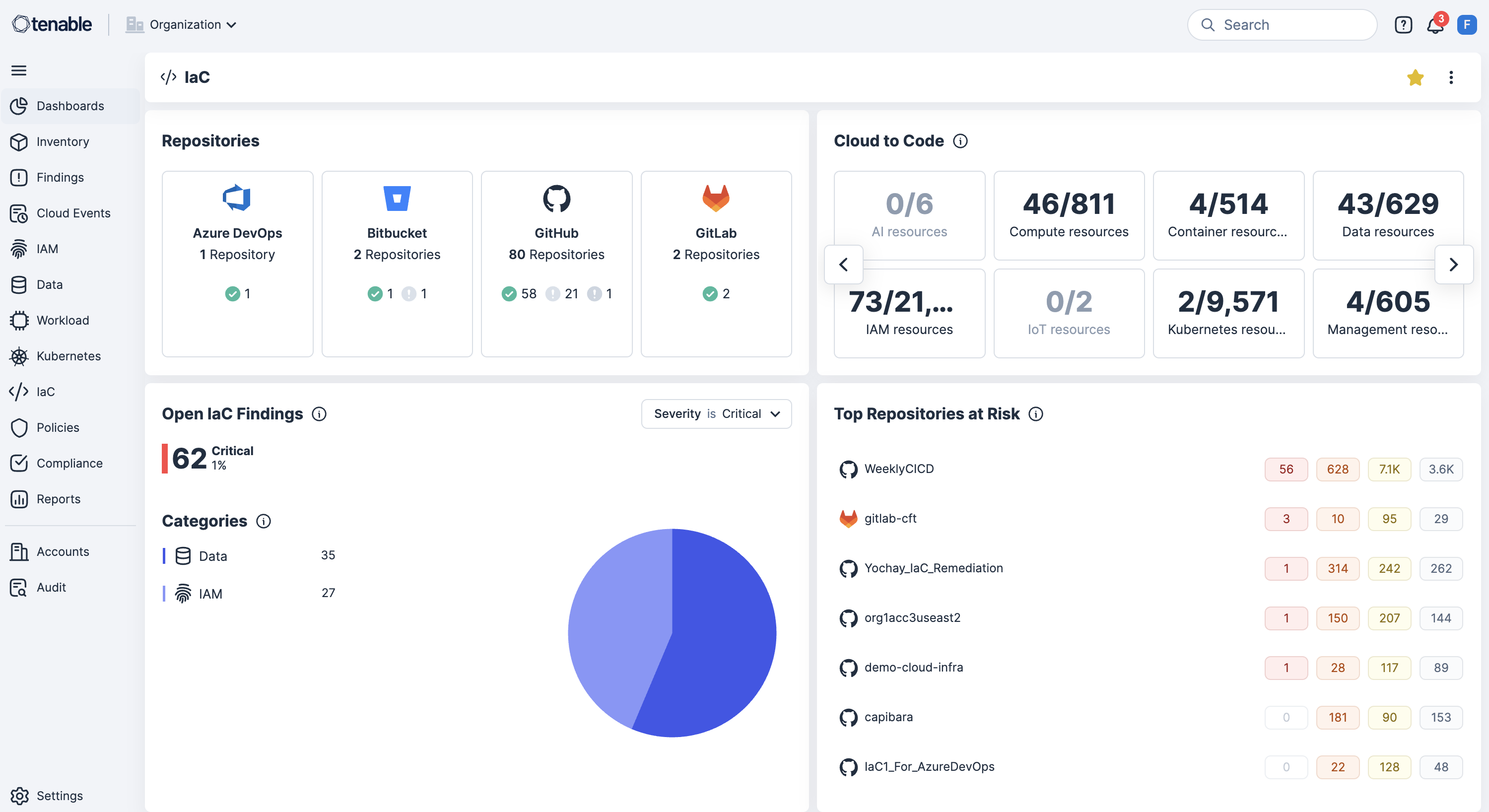
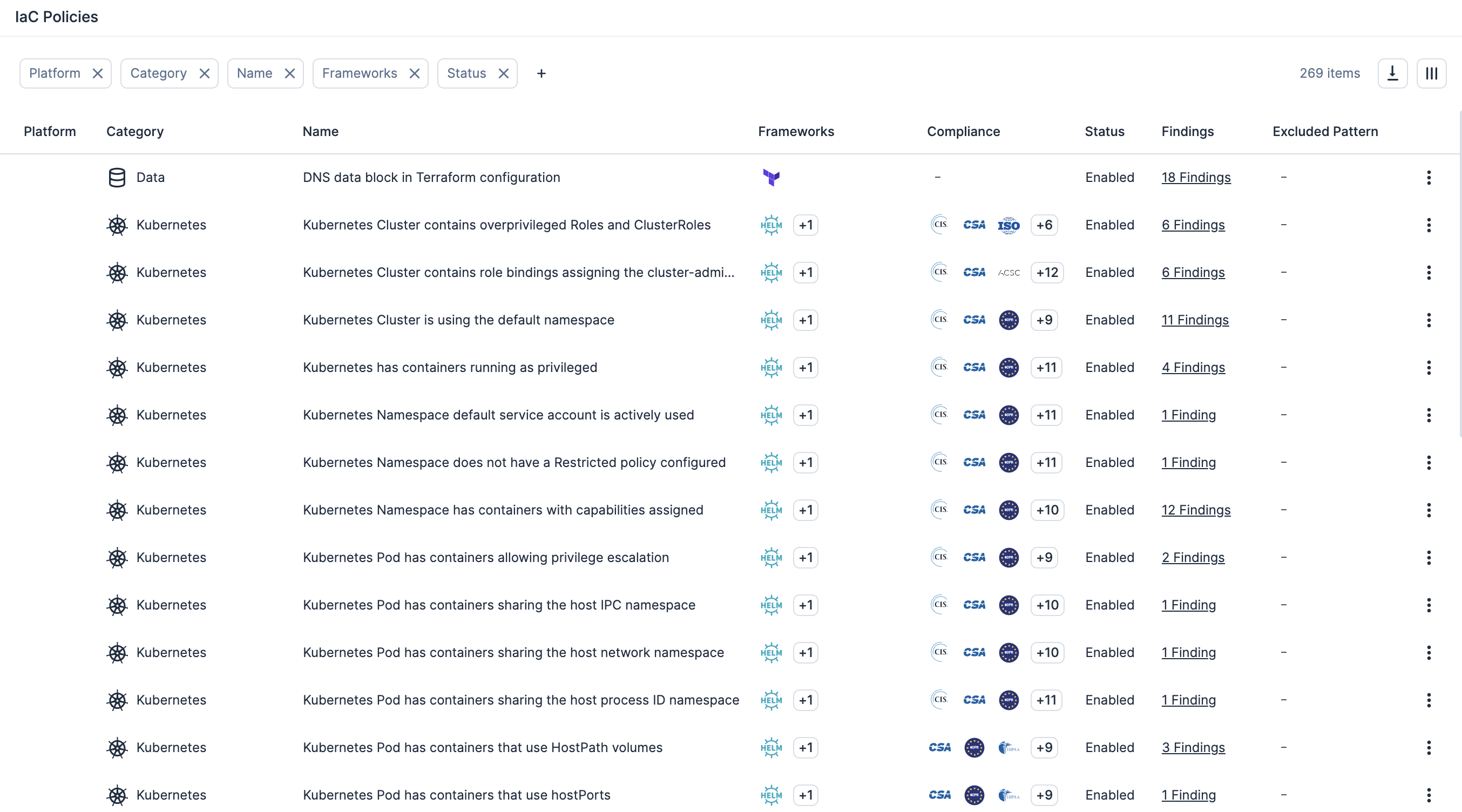
轻松识别和修复错误配置。云错误配置,如开放的存储桶、权限过度宽松的角色或不安全的网络设置,是导致数据外泄、合规性失败和数据丢失的主要原因。 使用 Tenable Cloud Security,通过基础上设施即代码 (IaC) 扫描持续检测这些风险并进行优先级分析,将防护覆盖整个运行时和身份层。
不受警报所限,实现自动化云安全
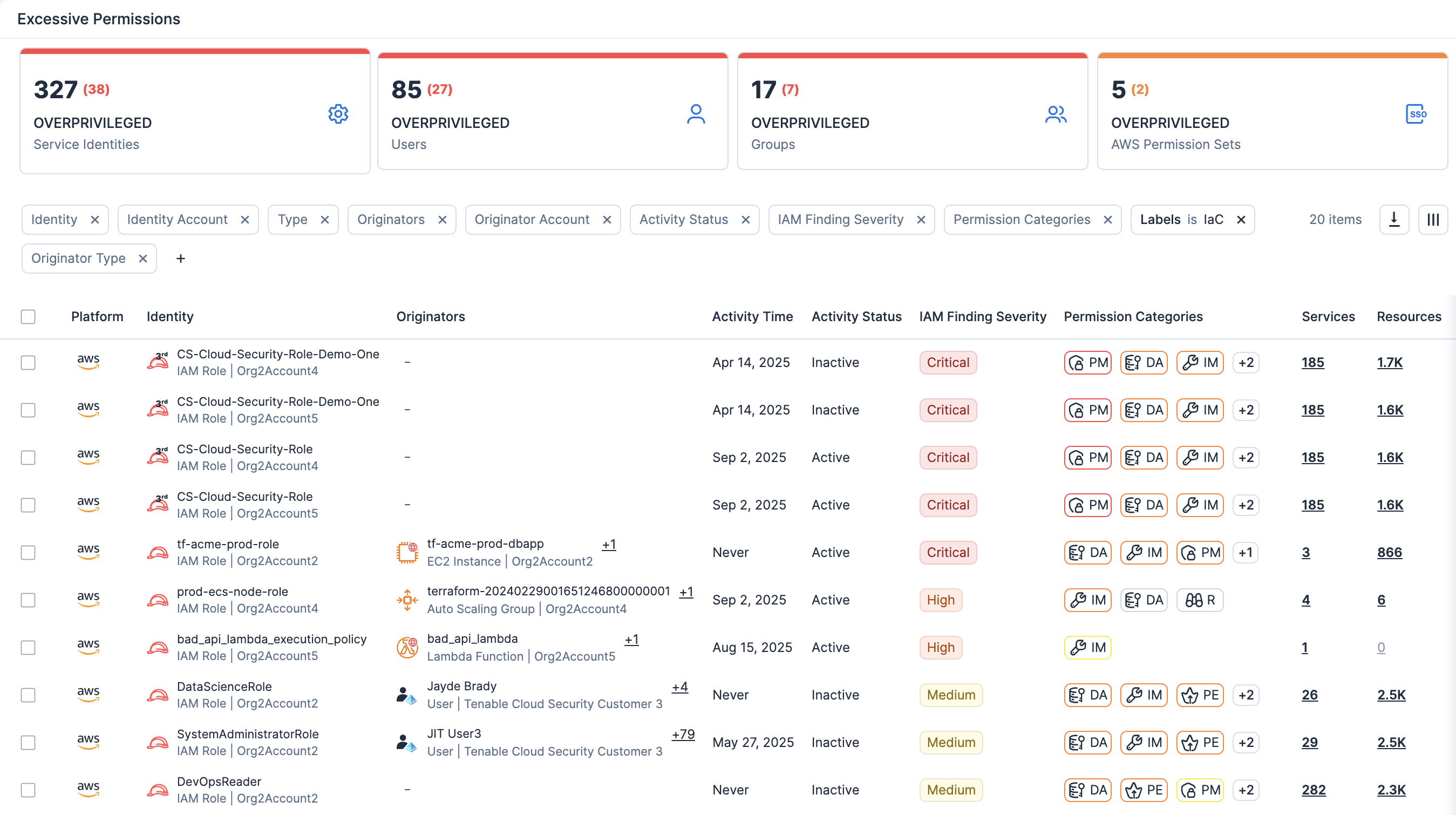
识别暴露的存储桶、权限过度宽松的角色以及不安全的网络设置。
对上下文风险关联明察秋毫,然后实施身份感知型修复
将错误配置与漏洞、过度权限和敏感数据暴露相关联,同时通过云基础设施权限管理 (CIEM) 映射身份,从而实施最小特权并加快修复速度。
了解更多关于 Tenable Cloud Security 的信息
用 [Tenable 的] 自动化技术可以让我们免去繁琐的人工流程,在几分钟内即可完成原本需要两三个安全人员花费好几个月才能完成的工作。
- Tenable Cloud Security