Frequently Asked Questions About SonicWall Gen 7 Firewall Ransomware Activity

An increase in ransomware activity tied to SonicWall Gen 7 Firewalls has been observed, possibly linked to the exploitation of a zero-day vulnerability in its SSL VPN.
Update August 7: The blog has been updated with the latest updates from SonicWall, noting that there has not been a new zero-day vulnerability identified.
Background
Tenable’s Research Special Operations (RSO) team has compiled this blog to answer Frequently Asked Questions (FAQ) regarding an increase in ransomware activity targeting SonicWall Gen 7 Firewalls.
FAQ
What is the ransomware activity being observed against SonicWall Gen 7 Firewalls?
Reports from researchers at Arctic Wolf and Huntress have noted an observable increase in attacks targeting SonicWall firewalls, specifically the Gen 7 (or seventh generation) firewalls. Both Arctic Wolf and Huntress assess that the ransomware activity is linked to the Akira ransomware.
When was this ransomware activity against SonicWall firewalls first observed?
Arctic Wolf observed an increase in activity at the end of July 2025, while Huntress has been responding to incidents in the first few days of August 2025.
What does this have to do with SonicWall’s SSL VPN and a zero-day vulnerability?
The ransomware activity has been observed on Gen 7 firewalls with SSL VPN enabled.
Researchers have noted that even if multifactor authentication is enabled, attackers have been able to compromise accounts on these devices. In some instances, the SonicWall devices are fully patched. These factors give credence to the likelihood that a zero-day vulnerability in these devices is being exploited.
In an update on August 6, SonicWall clarified that the recent activity "is not connected to a zero-day vulnerability." Instead, many the incidents they have investigated have been in devices that have migrated from Gen 6 to Gen 7 firewalls, where local user accounts were not reset as outlined in security advisory SNWLID-2024-0015. This advisory addresses CVE-2024-40766, an improper access control vulnerability which has been observed to have been exploited in the wild.
What are the vulnerabilities associated with this ransomware activity?
As of August 5, SonicWall has not yet assigned any CVEs for the ransomware activity. On August 6, SonicWall updated their threat activity notice indicating that threat activity is related to CVE-2024-40766.
Are there any other threat actors involved in this ransomware activity?
Right now, we are only aware of reports that the Akira ransomware has been leveraged in these attacks. We will update this blog post if or when additional ransomware activity, along with any other malicious activity, is observed.
Are patches or mitigations available for this ransomware activity?
SonicWall has published a threat activity notice on its website as it investigates the reports of malicious activity. The current guidance as of August 6 instructs customers using SonicWall Gen 7 firewalls who have imported configurations from Gen 6 to review the following guidance:
- Update firmware to version 7.3.0 which has "enhanced protections against brute force attacks and additional MFA controls."
- Reset all local user account passwords. This is especially important in cases where accounts with SSLVPN access were migrated from Gen 6 to Gen 7.
- Enforce multifactor authentication (MFA) for SSLVPN
- Audit accounts and identify unused or inactive accounts
- Use strong and unique passwords for user accounts
- Enable Botnet Protection and Geo-IP Filtering.
I thought that MFA was bypassed by the attackers, so why is that listed as a mitigation?
MFA is part of standard security guidance to thwart against common attack vectors, e.g. brute-force, credential stuffing or stolen credentials.
Has Tenable released any product coverage?
While no new CVE has been announced, the updated guidance as of August 6 is that observed threat activity is related to CVE-2024-40766. Tenable product coverage for CVE-2024-40766 can be found here.
Tenable customers can also utilize our SonicWall SonicOS detection plugin to identify Gen 7 devices on their networks.
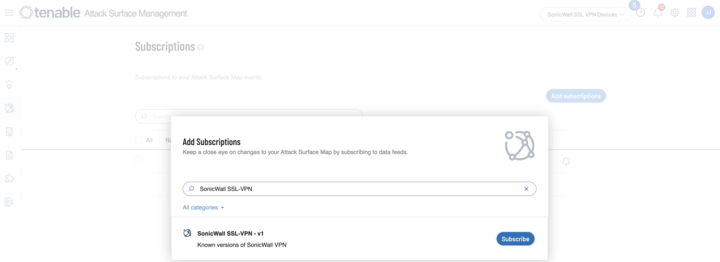
Additionally, Tenable Attack Surface Management customers can identify external-facing SonicWall assets with SSL VPN enabled by leveraging the built-in subscription labeled SonicWall SSL-VPN v1.
Change Log
Update August 7: The blog has been updated with the latest updates from SonicWall, noting that there has not been a new zero-day vulnerability identified.
Get more information
- Gen 7 SonicWall Firewalls – SSLVPN Recent Threat Activity
- Arctic Wolf Observes July 2025 Uptick in Akira Ransomware Activity Targeting SonicWall SSL VPN
- Huntress Threat Advisory: Active Exploitation of SonicWall VPNs
Join Tenable's Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


